Event Source Data Classes
Event Source Data Classes utility provides classes self-describing Lambda event sources.
Key Features¶
- Type hinting and code completion for common event types
- Helper functions for decoding/deserializing nested fields
- Docstrings for fields contained in event schemas
Background
When authoring Lambda functions, you often need to understand the schema of the event dictionary which is passed to the handler. There are several common event types which follow a specific schema, depending on the service triggering the Lambda function.
Getting started¶
Utilizing the data classes¶
The classes are initialized by passing in the Lambda event object into the constructor of the appropriate data class or
by using the event_source decorator.
For example, if your Lambda function is being triggered by an API Gateway proxy integration, you can use the
APIGatewayProxyEvent class.
1 2 3 4 5 6 | |
Same example as above, but using the event_source decorator
1 2 3 4 5 6 | |
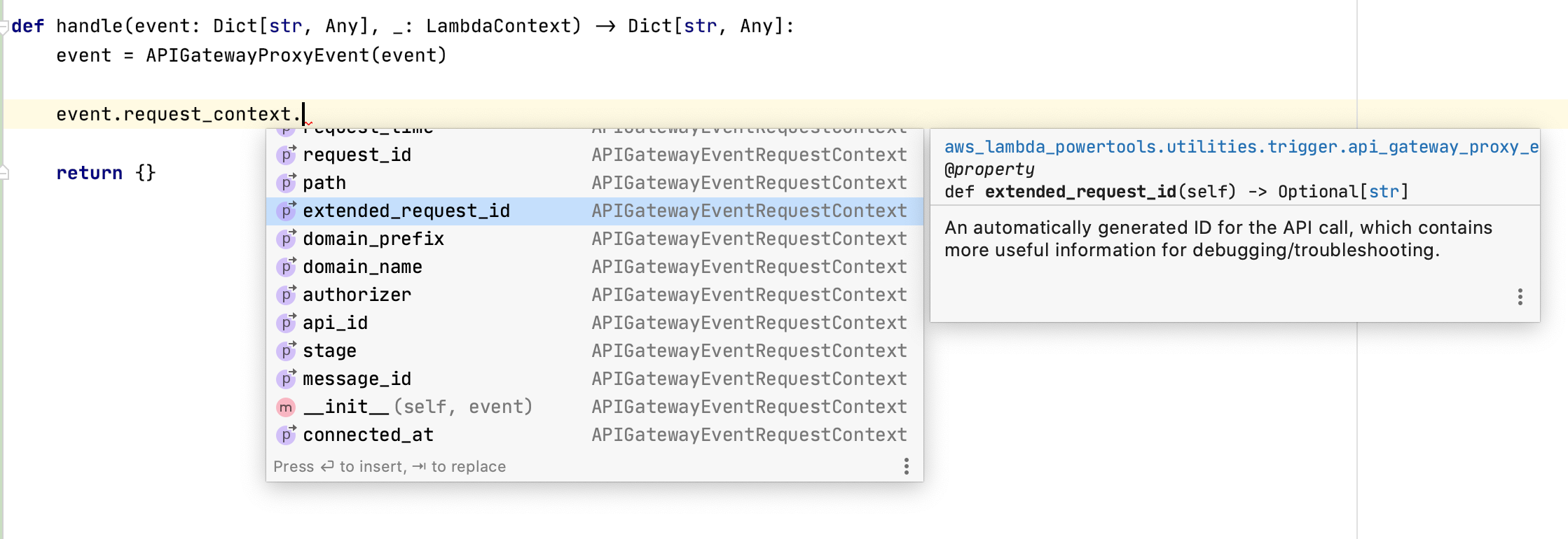
Autocomplete with self-documented properties and methods
Supported event sources¶
| Event Source | Data_class |
|---|---|
| Active MQ | ActiveMQEvent |
| API Gateway Authorizer | APIGatewayAuthorizerRequestEvent |
| API Gateway Authorizer V2 | APIGatewayAuthorizerEventV2 |
| API Gateway Proxy | APIGatewayProxyEvent |
| API Gateway Proxy V2 | APIGatewayProxyEventV2 |
| Application Load Balancer | ALBEvent |
| AppSync Authorizer | AppSyncAuthorizerEvent |
| AppSync Resolver | AppSyncResolverEvent |
| CloudWatch Dashboard Custom Widget | CloudWatchDashboardCustomWidgetEvent |
| CloudWatch Logs | CloudWatchLogsEvent |
| CodePipeline Job Event | CodePipelineJobEvent |
| Cognito User Pool | Multiple available under cognito_user_pool_event |
| Connect Contact Flow | ConnectContactFlowEvent |
| DynamoDB streams | DynamoDBStreamEvent, DynamoDBRecordEventName |
| EventBridge | EventBridgeEvent |
| Kafka | KafkaEvent |
| Kinesis Data Stream | KinesisStreamEvent |
| Kinesis Firehose Delivery Stream | KinesisFirehoseEvent |
| Lambda Function URL | LambdaFunctionUrlEvent |
| Rabbit MQ | RabbitMQEvent |
| S3 | S3Event |
| S3 Object Lambda | S3ObjectLambdaEvent |
| SES | SESEvent |
| SNS | SNSEvent |
| SQS | SQSEvent |
Info
The examples provided below are far from exhaustive - the data classes themselves are designed to provide a form of documentation inherently (via autocompletion, types and docstrings).
Active MQ¶
It is used for Active MQ payloads, also see the AWS blog post for more details.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | |
API Gateway Authorizer¶
New in 1.20.0
It is used for API Gateway Rest API Lambda Authorizer payload.
Use APIGatewayAuthorizerRequestEvent for type REQUEST and APIGatewayAuthorizerTokenEvent for type TOKEN.
This example uses the APIGatewayAuthorizerResponse to decline a given request if the user is not found.
When the user is found, it includes the user details in the request context that will be available to the back-end, and returns a full access policy for admin users.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | |
API Gateway Authorizer V2¶
New in 1.20.0
It is used for API Gateway HTTP API Lambda Authorizer payload version 2. See also this blog post for more details.
This example looks up user details via x-token header. It uses APIGatewayAuthorizerResponseV2 to return a deny policy when user is not found or authorized.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | |
API Gateway Proxy¶
It is used for either API Gateway REST API or HTTP API using v1 proxy event.
1 2 3 4 5 6 7 8 9 | |
API Gateway Proxy V2¶
It is used for HTTP API using v2 proxy event.
1 2 3 4 5 6 | |
Application Load Balancer¶
Is it used for Application load balancer event.
1 2 3 4 5 6 | |
AppSync Authorizer¶
New in 1.20.0
Used when building an AWS_LAMBDA Authorization with AppSync. See blog post Introducing Lambda authorization for AWS AppSync GraphQL APIs or read the Amplify documentation on using AWS Lambda for authorization with AppSync.
In this example extract the requestId as the correlation_id for logging, used @event_source decorator and builds the AppSync authorizer using the AppSyncAuthorizerResponse helper.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 | |
AppSync Resolver¶
New in 1.12.0
Used when building Lambda GraphQL Resolvers with Amplify GraphQL Transform Library (@function),
and AppSync Direct Lambda Resolvers.
In this example, we also use the new Logger correlation_id and built-in correlation_paths to extract, if available, X-Ray Trace ID in AppSync request headers:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | |
CloudWatch Dashboard Custom Widget¶
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 | |
CloudWatch Logs¶
CloudWatch Logs events by default are compressed and base64 encoded. You can use the helper function provided to decode, decompress and parse json data from the event.
1 2 3 4 5 6 7 8 9 | |
CodePipeline Job¶
Data classes and utility functions to help create continuous delivery pipelines tasks with AWS Lambda
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 | |
Cognito User Pool¶
Cognito User Pools have several different Lambda trigger sources, all of which map to a different data class, which
can be imported from aws_lambda_powertools.data_classes.cognito_user_pool_event:
| Trigger/Event Source | Data Class |
|---|---|
| Custom message event | data_classes.cognito_user_pool_event.CustomMessageTriggerEvent |
| Post authentication | data_classes.cognito_user_pool_event.PostAuthenticationTriggerEvent |
| Post confirmation | data_classes.cognito_user_pool_event.PostConfirmationTriggerEvent |
| Pre authentication | data_classes.cognito_user_pool_event.PreAuthenticationTriggerEvent |
| Pre sign-up | data_classes.cognito_user_pool_event.PreSignUpTriggerEvent |
| Pre token generation | data_classes.cognito_user_pool_event.PreTokenGenerationTriggerEvent |
| User migration | data_classes.cognito_user_pool_event.UserMigrationTriggerEvent |
| Define Auth Challenge | data_classes.cognito_user_pool_event.DefineAuthChallengeTriggerEvent |
| Create Auth Challenge | data_classes.cognito_user_pool_event.CreateAuthChallengeTriggerEvent |
| Verify Auth Challenge | data_classes.cognito_user_pool_event.VerifyAuthChallengeResponseTriggerEvent |
Post Confirmation Example¶
1 2 3 4 5 6 7 | |
Define Auth Challenge Example¶
Note
In this example we are modifying the wrapped dict response fields, so we need to return the json serializable wrapped event in event.raw_event.
This example is based on the AWS Cognito docs for Define Auth Challenge Lambda Trigger.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 | |
Create Auth Challenge Example¶
This example is based on the AWS Cognito docs for Create Auth Challenge Lambda Trigger.
1 2 3 4 5 6 7 8 9 10 | |
Verify Auth Challenge Response Example¶
This example is based on the AWS Cognito docs for Verify Auth Challenge Response Lambda Trigger.
1 2 3 4 5 6 7 8 9 | |
Connect Contact Flow¶
New in 1.11.0
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
DynamoDB Streams¶
The DynamoDB data class utility provides the base class for DynamoDBStreamEvent, as well as enums for stream view type (StreamViewType) and event type.
(DynamoDBRecordEventName).
The class automatically deserializes DynamoDB types into their equivalent Python types.
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
1 2 3 4 5 6 7 8 9 10 | |
EventBridge¶
1 2 3 4 5 | |
Kafka¶
This example is based on the AWS docs for Amazon MSK and self-managed Apache Kafka.
1 2 3 4 5 6 | |
Kinesis streams¶
Kinesis events by default contain base64 encoded data. You can use the helper function to access the data either as json or plain text, depending on the original payload.
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
Kinesis Firehose delivery stream¶
Kinesis Firehose Data Transformation can use a Lambda Function to modify the records inline, and re-emit them back to the Delivery Stream.
Similar to Kinesis Data Streams, the events contain base64 encoded data. You can use the helper function to access the data either as json or plain text, depending on the original payload.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | |
Lambda Function URL¶
1 2 3 4 5 | |
Rabbit MQ¶
It is used for Rabbit MQ payloads, also see the blog post for more details.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | |
S3¶
1 2 3 4 5 6 7 8 9 10 11 12 | |
S3 Object Lambda¶
This example is based on the AWS Blog post Introducing Amazon S3 Object Lambda – Use Your Code to Process Data as It Is Being Retrieved from S3.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | |
SES¶
1 2 3 4 5 6 7 8 9 10 | |
SNS¶
1 2 3 4 5 6 7 8 9 10 | |
SQS¶
1 2 3 4 5 6 7 | |